GCP
Overview
Note
For feedback, questions, and comments — please open a GitHub Issue.
Please review the Project Support section for important information on support and service terms.
The Security Reference Architecture (SRA) with Terraform provides a prescriptive deployment pattern for Databricks on GCP, designed for highly secure and regulated environments. It captures Databricks security best practices in Terraform templates, allowing organizations to programmatically deploy workspaces and supporting infrastructure with hardened, opinionated defaults.
This architecture emphasizes:
- Secure by Default – Deployments leverage customer-managed VPCs, Private Service Connect (PSC), and customer-managed encryption keys (CMEK) to ensure all data plane and control plane communication remains within Google’s private network and under customer control.
- Governance & Compliance – esigned to meet stringent enterprise and regulatory requirements by standardizing secure network boundaries, key management, and private connectivity through reusable Terraform modules.
- Scalability – Uses a modular network foundation that supports multiple workspaces across shared VPCs, enabling consistent security enforcement, resource isolation, and simplified lifecycle management.
- Point-in-Time Design – Each release reflects security best practices at that time; new releases may not be drop-in replacements.
Architecture Diagram
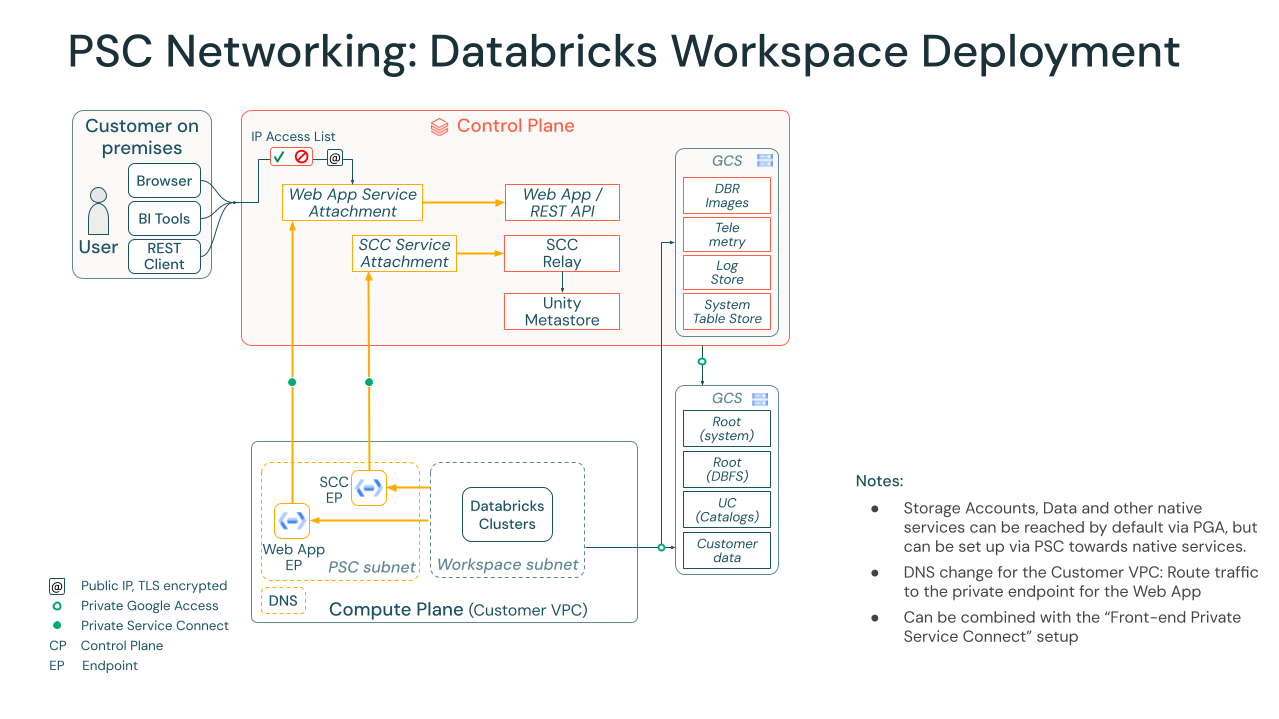
The GCP implementation of the Security Reference Architecture (SRA) includes:
- A customer managed VPC model for centralized network management, workload isolation, and simplified multi-workspace connectivity.
- Core GCP components such as customer-managed VPCs, Private Service Connect (PSC) for back-end connectivity, Cloud KMS for customer-managed encryption keys (CMEK), and Private Cloud DNS for internal name resolution.
Next Steps
- Review the Read Before Deploying section for critical considerations.
- Explore the SRA Components Breakdown to understand the included GCP and Databricks resources.
- Follow the Getting Started guide to deploy using Terraform.